Information checkedInformation unaudited Information geprüft Information ungeprüft “Act as if it were your own data”


According to the International Monetary Fund, one in five cyberattacks is now directed at the financial sector. This entails the risk of enormous damage – both material and intangible alike. That is why Head of Business Risk Management Jousry Abdel-Khalek and his team work day in, day out to ensure that LLB escapes unscathed. In this interview, he explains how this works.
Jousry, can you briefly introduce yourself and your team?
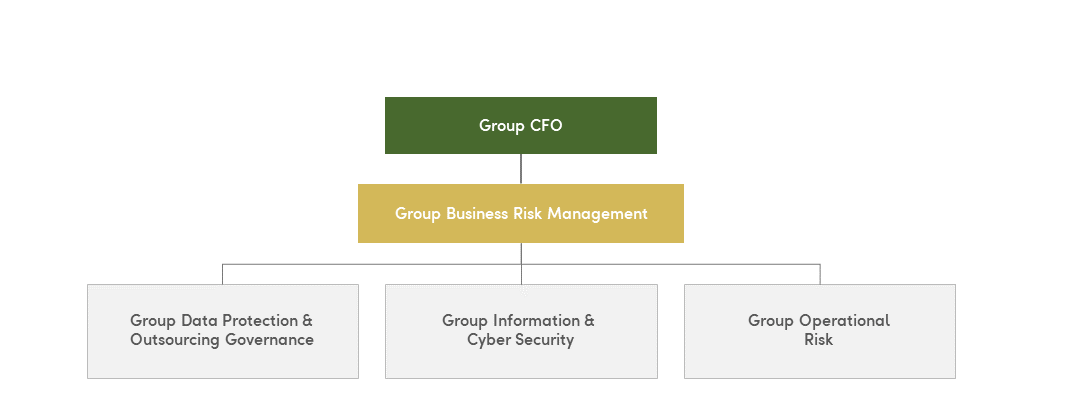
I joined the LLB Group as Head of the Business Risk Management unit and Group CISO in January 2020. The unit is divided into three parts – operational risk, data protection & outsourcing and information & cyber security – and is home to a total of fifteen employees. You can also find in-depth information about our area and our remit on the intranet.
)
JP Morgan has published figures stating that it is affected by billions of cyberattacks every day. What about us?
We’re noticing an uptick in the financial centre of Liechtenstein. One explanation might be that hackers are looking for new victims. JP Morgan, UBS and the like are now on a good footing security-wise. The attacks are therefore now being directed at smaller financial institutions and other sectors, such as industry.
What exactly happens when an attack on our systems is detected?
For example, we are notified by the department (say, by a client adviser) that the incident has taken place. And, depending on the situation, we will then take appropriate countermeasures. If it’s a broad-based attack, we also respond in broad terms. If, conversely, it was a targeted incident, defensive measures are put in place at that exact spot. Further bodies, such as the police, will be involved if appropriate. As a private institution, we aren’t entitled to actively hunt down criminals or to infiltrate other systems. We are entitled to (and do) protect our systems and clients by sealing ourselves off.
Cybercrime isn’t a new phenomenon: hackers already had plenty of time to perfect their skills and their methods. How can we counter this as a relatively small unit?
Of course, the attackers are one step ahead of us. But we try to avoid letting them get too far in front, to the extent that we can. That said, the resources and capacities that the big players, particularly state attackers, have at their disposal are huge and varied.
So, are we left totally unprotected and defenceless?
Let me put your mind at rest: no, of course not. We can still do a great deal. For example, by developing secure applications, testing our systems and asking ourselves over and over again: can we do things even better? Or by employing ethical hackers to use so-called red-teaming ambushes to attack our systems and thus reveal potential vulnerabilities. Furthermore, thanks to our membership of various associations and networks, we can benefit from their know-how, size and cooperation.
It’s not uncommon for malware or similar to be sent to companies via e-mail and cause immense damage. How do you rate this means of communication? Is it a blessing or a curse?
Honestly? I’d like to see a lot less e-mail being sent and, instead, more one-to-one conversations – whether that’s a phone call or going for a coffee. After all, with every e-mail not sent and every attachment that goes unopened, the risk of data ending up in the wrong hands is reduced.
What’s the biggest vulnerability in our security environment?
It’s clear: human beings are our biggest vulnerability. We’re all emotional and social beings. This also means that we’re sometimes too friendly and can be taken by surprise. It starts with me guiding someone I don’t know through a locked door. Once inside, criminals have already overcome their first hurdle. A second point is that we want social interaction, we talk to each other. Of course, it’s important that I pay attention to what I’m saying and to whom I’m saying it. Data security doesn’t just start with our laptops.
What can we do about this?
Constantly provide information, raise awareness and run training until everyone understands how important this topic is. When providing information and data, always check whether the recipient is authorised to receive it.
The multi-year “Cyber” Group project is also a testament to the importance of data security within the LLB Group. This has now been completed. How did it go and what is your conclusion?
One key objective of the project was to increase our ability to respond in the event of a cyberattack. In addition, new processes for continuous vulnerability analysis were to be defined and introduced. I can say that we’ve succeeded in this: thanks to the project, we’ve significantly increased our cyber defence capacity through technical measures. When the systems now behave unusually, an alarm goes off immediately. This allows us to intervene much earlier, whether in the case of unusual network activities or even when we are attacked. For instance, the fact that we’ve really taken a step forward in this regard was also shown during the last “planned” red-teaming session, when we were able to defend against the attack much sooner and much better.
Does that mean this is all done with?
No, of course not. Cyber security is a process that can’t be wrapped up in a single project. Every activity or attack gives us the chance to scrutinise our processes and measures so we can respond to future issues better. Further measures are also being rolled out, such as advanced pentest activities.
At present, we can say, of course, that we’ve been spared from major attacks so far. Do we really need to expend all this effort?
This question can be answered quickly if we take a look at what, in the worst case, could happen to us in the event of a severe cyberattack: one scenario, for example, would be that our payment system is attacked by ransomware, a kind of encryption software, and we lose our data integrity. This would mean that we’d be excluded from payment transactions and would no longer be able to make payments. This would have serious consequences for Liechtenstein itself. Another possible scenario would be an actual data theft, with the stolen data then appearing on the dark net. Of course, this would be associated with an immense loss of trust. So is the effort really worth it? Definitely!
Have we fallen victim to cases like these?
No, luckily not. That said, our clients have been the targets of attacks, such as via phishing or similar.
If a genie gave you one wish, what would it be?
I would like every single one of us to take a much closer look at how we handle data: in other words, does XY really need to receive this data in order to fulfil their tasks? Maybe a leaner collection of information, without an assortment of co-recipients in CC, would suffice? And vice versa: do I know the sender and am I expecting their e-mail? Or, drawing on our culture journey KEO: act as if it were your own data.


